FortiGate
You can configure FortiGate to send logs to Logmanager through GUI or CLI configuration.
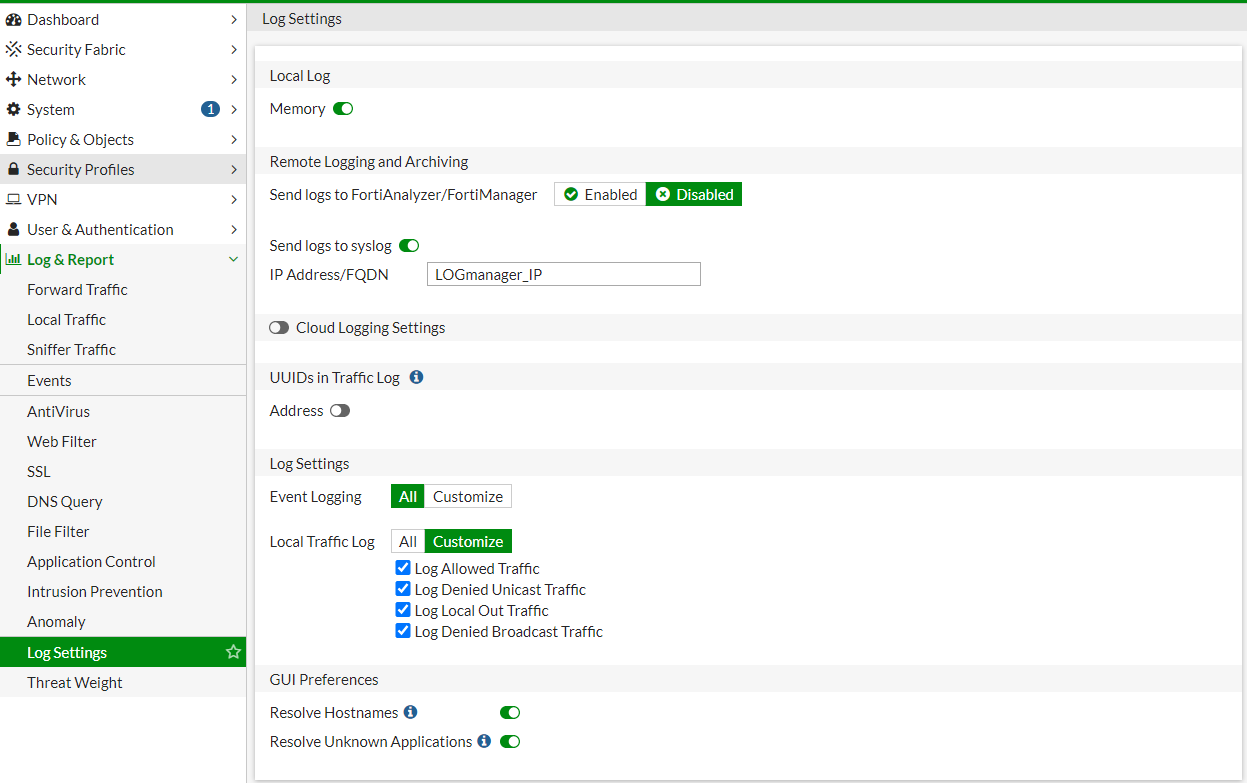
Configuring via GUI
Logmanager_IP_address is the IP address of your Logmanager server.
For log collecting from FortiGate device please follow next few steps.
Login to FortiGate device via CLI and set the following commands:
FortiGate # conf log syslogd setting
FortiGate (setting) # set status enable
FortiGate (setting) # set server "<Logmanager_IP_address>"
FortiGate (setting) # show
config log syslogd setting
set status enable
set server "<Logmanager_IP_address>"
set source-ip "<FortiGate_IP_address>"
end
FortiGate (setting) # end
Logmanager_IP_address is the IP address of your Logmanager server.
FortiGate_IP_address is the IP address of your FortiGate device.
FortiOS version 6.x is in default settings sending interim updates on every firewall session that is open and set to logging. This can cause huge increase in number of messages sent by FortiGate. Reason is that instead of one log message on end of every sessions, each session is logged multiple times with increasing counters of transmited data (ex: web session of 30minutes on webserver can cause 30logs instead of 1).
To disable this behaviour use this configuration:
config log syslogd filter
set filter "logid(20)"
set filter-type exclude
end
The default logging scheme and sending logs to syslog is not quite optimal. By default, FortiOS logs the following:
- Start of session
- Session progress, every few minutes
- End of session
This means that if you have for example, a long running session (which survives cluster restarts), it generates a large volume of traffic, which can break the appearance of the Traffic dashboards.
Examplelog:
<189>date=2023-03-30 time=15:10:32 devname="fortigate" devid="FGTXXXXXXXXXX" eventtime=1680181831275545540 tz="+0200" logid="0000000020" type="traffic" subtype="forward" level="notice" vd="logmanager" srcip=192.0.0.20 srcport=5800 srcintf="interface" srcintfrole="lan" dstip=192.0.0.112 dstport=51100 dstintf="interface" dstintfrole="lan" srccountry="Reserved" dstcountry="Reserved" sessionid=89863 proto=17 action="accept" policyid=1 policytype="policy" poluuid="921f6344-c8e9-51ed-6b51-36e37acbdaf5" policyname="policy_name" service="udp/51100" trandisp="noop" duration=264373 sentbyte=46193641625 rcvdbyte=0 sentpkt=61293266 rcvdpkt=0 appcat="unscanned" sentdelta=25083758 rcvddelta=0 devtype="Router" mastersrcmac="00:00:00:00:00:00" srcmac="00:00:00:00:00:00" srcserver=0
If you choose to drop this information, you can save 10 to 80% (depending on traffic) of the log events from FortiGate.
Configuring optimization from the CLI:
config log syslogd filter
config free-style
edit 1
set category traffic
set filter "(logid 0000000020)"
set filter-type exclude
next
end
end