SSL certificates
The SSL certificates menu works with SSL Certificates in Logmanager system. Certificates can be imported into the system, and then a Certificate signing request and self-signed certificate can be created. SSL certificates are then used in section System ‣ SSL certificates for individual Logmanager server services. Logmanager contains its own self-signed certificate by default, which is set for all services needing a certificate.
It is recommended to use server a certificate that has been signed by a trusted certificate authority for your Logmanager server. It is possible to use self-signed certificates, but they are usually insecure.
Supported certificates and keys are in the PEM and DER formats.
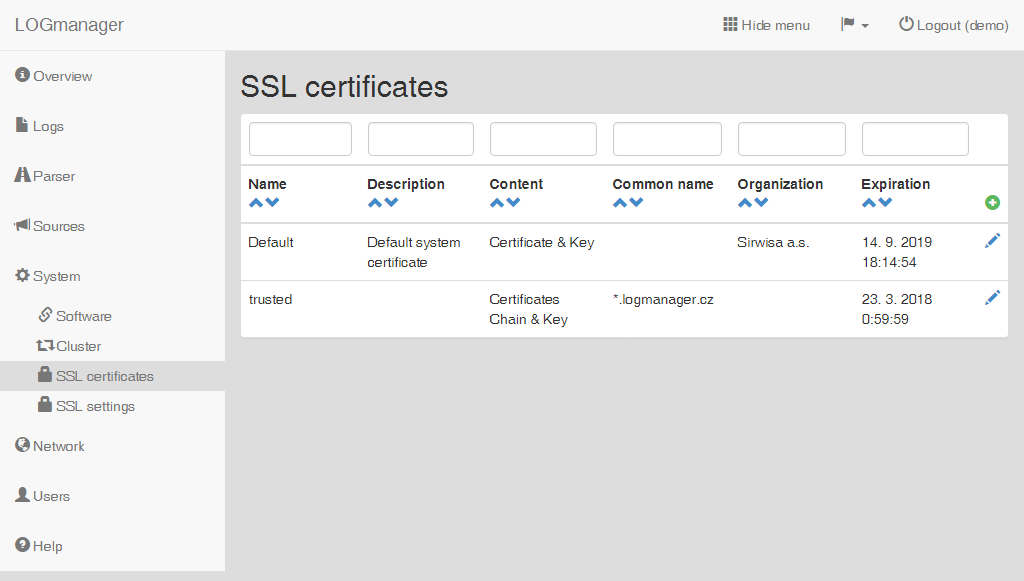
Certificates
The following table shows all available information:
- The name of the certificate (Name)
- The description of the certificate (Description)
- The contents of the certificate (Content)
- The CN name (Common name)
- The name of the organization (Organization)
- An expiration date (Expiration)
Filter fields are above the table. Data may be filtered by any single column. If you use filters in multiple columns, it is assumed that you are filtering using both. For example, if you choose Name and Common Name, it means that you want to filter by both the name and the Common Name.
Enter the following data into the prepared form:
- Name: name of the certificate.
- Description: description of the certificate.
- Type: choose
Certificate. - Certificate file: selection of the file with certificate, any file can be selected.
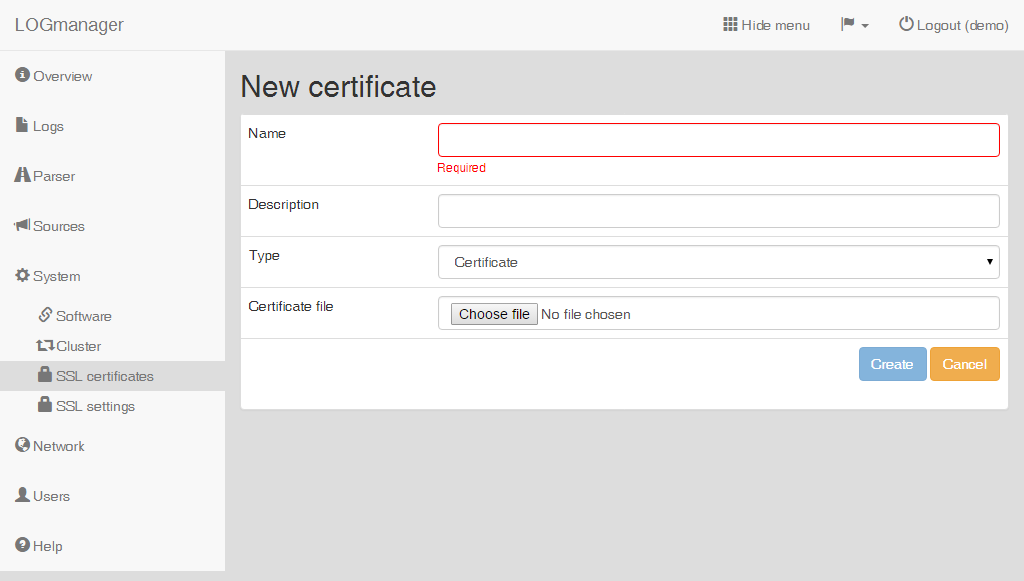
Adding a certificate
The Certificate system then performs a validity check on the uploaded certificate after the creation of the record. If the certificate is corrupted or not in the correct format, the system returns a certificate error.
Enter the following data into the prepared form:
- Name: name of the key.
- Description: description of the key.
- Type: choose
Key. - Key file: selection of the file with key, any file can be selected.
- Password: password to the key.
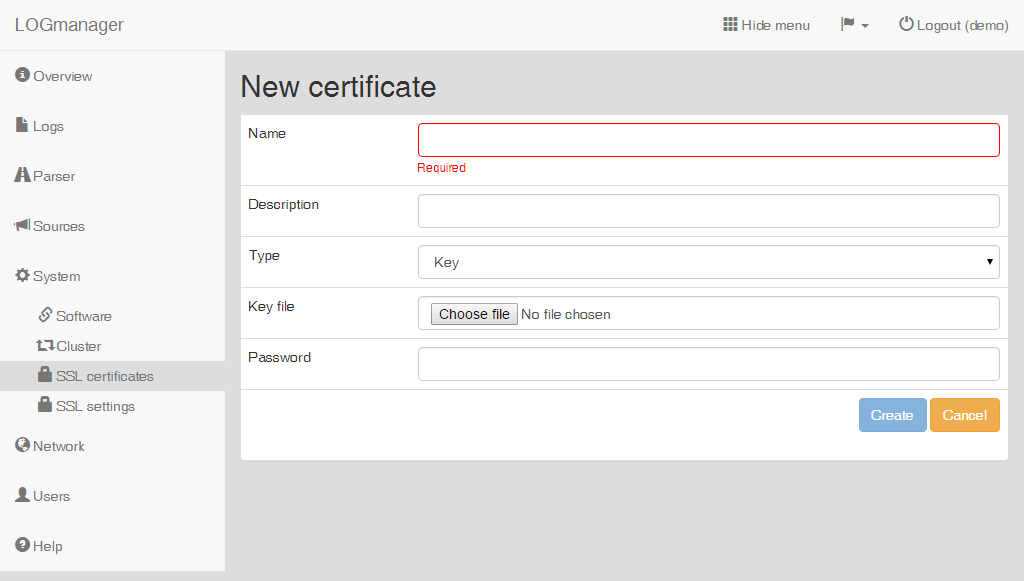
Adding a new key
The system performs a validity check of the uploaded key after the creation of the record, if the certificate is corrupted or in the wrong format, it will return a key error.
This option only combines the previous two options - separate certificate file and separate key file can be uploaded. Both files are merged into one certificate after creation.
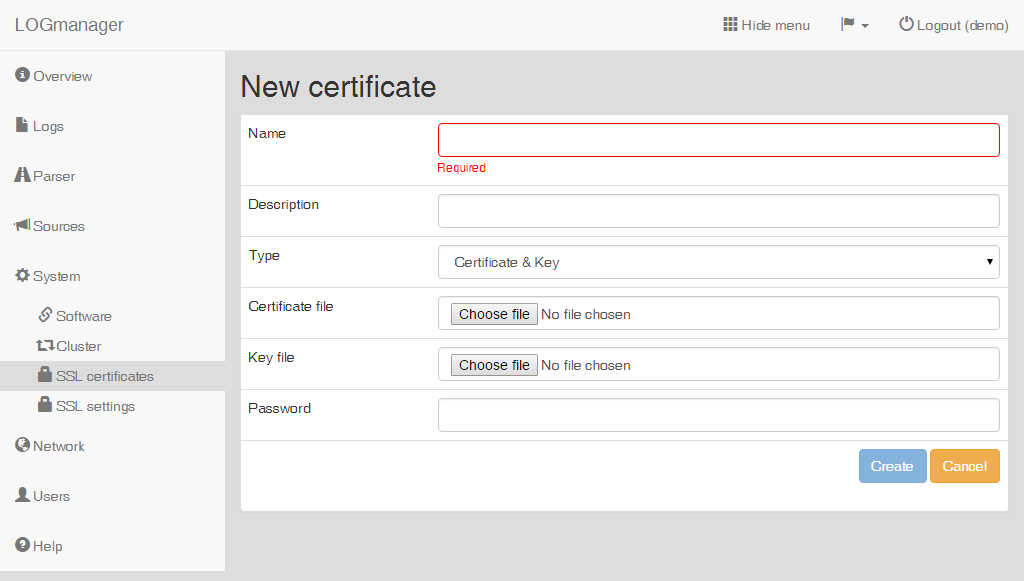
Adding a new certificate and key
It is recommended to follow these steps when requesting a new server certificate to increase the security of the certificates.
- Create a new CSR request,
- Use the public part to create a certificate at a certification authority,
- Insert the generated certificate from the certification authority into the CSR request.
Enter the following data into the prepared form:
- Name: name of the request.
- Description: description of the request.
- Type: choose
Request. - Common name: name of the domain.
- Organization: name of the company.
- Organizational unit: company department or purpose of the certificate.
- Locality: city (Prague).
- State or province: state (Czech republic).
- Country: country code (CZ).
- Email address: optional.
- Password: optional.
- Confirm password: password confirmation.
- Size: security level of the certificate.
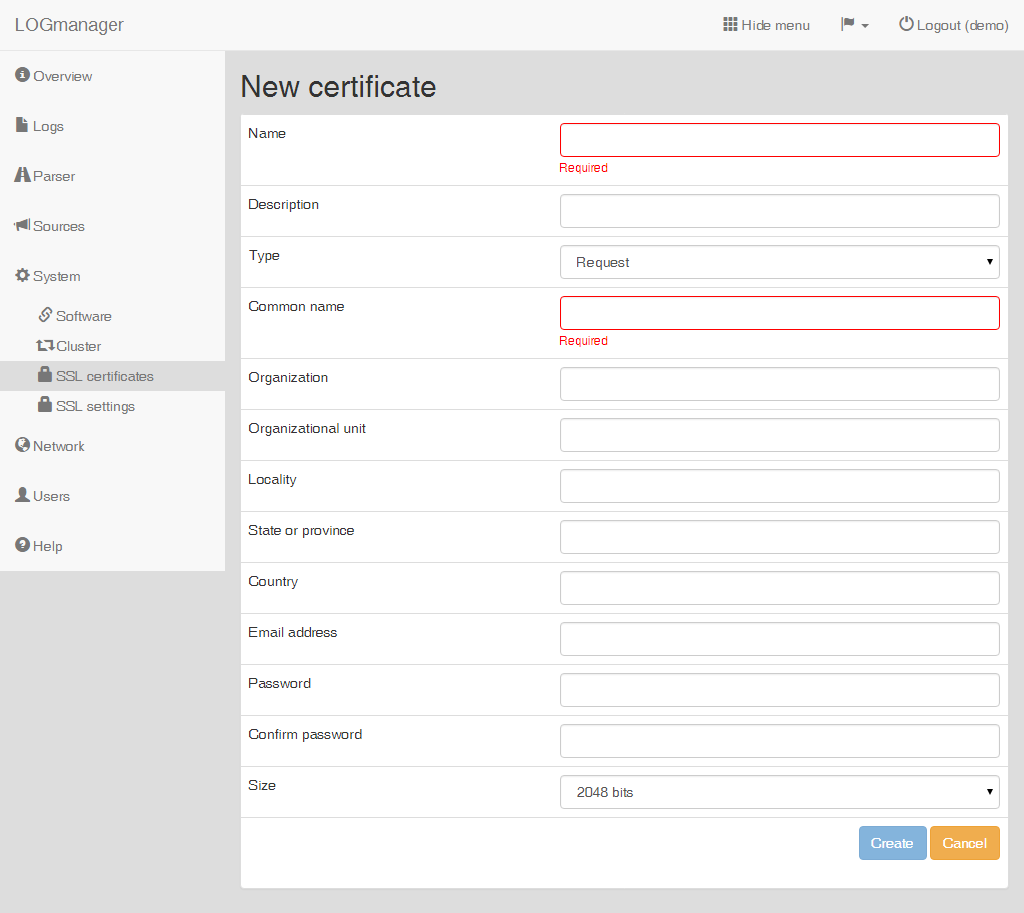
Creating a new CSR request
Logmanager allows you to also create a self-signed certificate. This certificate should not be considered trusted because it is signed by itself without a certification authority.
Enter the following data into the prepared form:
- Name: name of the request.
- Description: description of the request.
- Type: choose
Self-signed. - Common name: name of the domain.
- Organization: name of the company.
- Organizational unit: company department or purpose of the certificate.
- Locality: city (Prague).
- State or province: state (Czech republic).
- Country: country code (CZ).
- Email address: optional.
- Lifetime: value in days.
- Size: security level of the certificate.
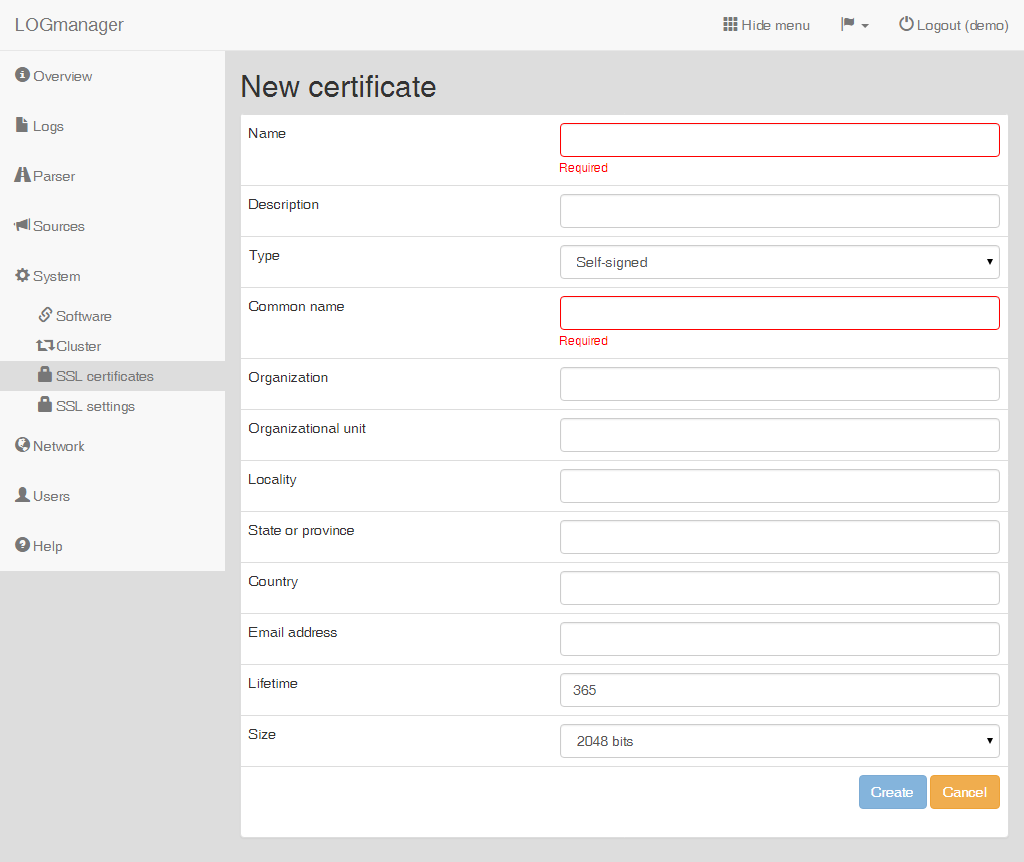
Creating a self-signed certificate
When working with a cluster of two or more nodes, it is not necessary for you to create certificates for each node. Certificates are created for a cluster as a whole and will be automatically synchronized to each node in the cluster.