Hillstone NGFW
Logging is a feature that records various kinds of system logs, including device log, threat log, session log, NAT log, File filter log, Network Behavior Record logshare access logs, and URL logs.
- Device log
- Event - includes 8 severity levels: debugging, information, notification, warning, error, critical, alert, emergency.
- Network - logs about network services, like PPPoE and DDNS.
- Configuration - logs about configuration on command line interface, e.g. interface IP address setting.
- Share Access Logs - logs about share access rule.
- Threat - logs related to behaviors threatening the protected system, e.g. attack defense and application security.
- Session - Session logs, e.g. session protocols, source and destination IP addresses and ports.
- NAT - NAT logs, including NAT type, source and destination IP addresses and ports.
- EPP - logs related with end point protection function.
- File Filter - logs related with file filter function.
- Network behavior record logs – Logs related with network behavior record function, e.g. IM behavior, etc.
- URL - logs about network surfing, e.g. Internet visiting time, web pages visiting history, an URL filtering logs.
- PBR - logs about policy-based route.
- CloudSandBox - logs about sandbox.
The system logs the running status of the device, thus providing information for analysis and evidence.
As displayed in the screenshot below. All needed on NGFW is just to define the destination of syslog and select all sources (or select the sources customer is interested in). Logging protocol suggested over TCP and destination port 514.
Hillstone config
To configure parameters of various log types, take the following steps:
- Select Monitor > Log > Log Management.
- Click on the tab of the log type you want, and you will enter the corresponding log settings.
- Click OK.
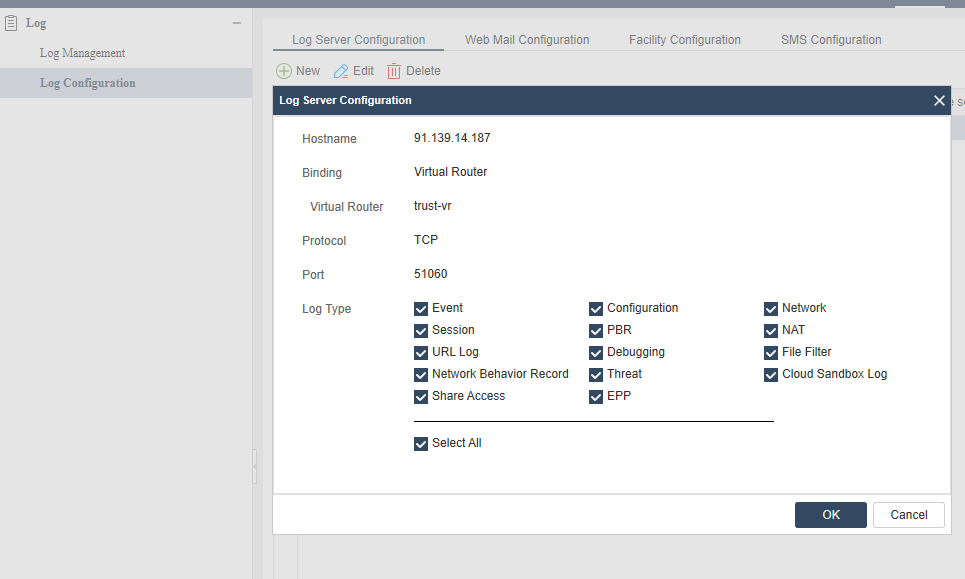
To create a log server, take the following steps:
- Select Monitor > Log > Log Configuration.
- Click Log Server Configuration tab.
- Click New.
In the Log Server Configuration dialog box, configure these values:
- Hostname: Enter the name or IP of the log server.
- Binding: Specifies the source IP address to receive logs.
- Virtual Router: Select Virtual Router and then select a virtual router form the drop-down list. If a virtual router is selected, the device will determine the source IP address by searching the reachable routes in the virtual router.
- Source Interface: Select Source Interface and then select a source interface from the drop-down list. The device will use the IP address of the interface as the source IP to send logs to the syslog server. If management IP address is configured on the interface, the management IP address will be preferred.
- Protocol: Specifies the protocol type of the syslog server. If “Secure-TCP” is selected, you can select Do not validate the server certificate option, and system can transfer logs normally and does not need any certifications.
- Port: Specifies the port number of the syslog server.
- Log Type: Specifies the log types the syslog server will receive.